Sign up for FlowVella
Sign up with FacebookAlready have an account? Sign in now
By registering you are agreeing to our
Terms of Service
Loading Flow


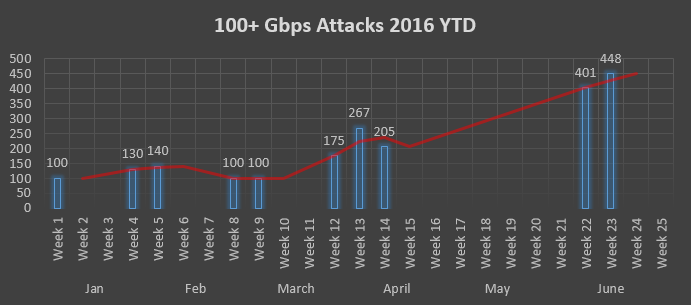
“The F5 SOC (Security Operations Center ) observed a sizeable 448 Gbps UDP/ICMP fragmentation flood destined primarily towards one specific subnet,” said Nic Garmendia, the F5 SOC analyst who monitored the attack, making sure mitigation was in place. “It ramped up extremely quickly and dropped drastically back down over the length of about nine minutes. As is common in UDP floods, the attackers sent highly-spoofed UDP packets at a very high packet rate using a large distributed source IP range. In this specific attack, over 100,000 IP addresses were used. Human intervention in order to apply mitigation was unnecessary upon detection as UDP ACLs began dropping the attack at the border.”